9 Most Deadliest Computer Viruses that Stood the Test of Time
computer virus history, computer virus examples
computer virus definition, computer virus examples, computer virus history, computer virus names, computer virus
what exactly is a Computer Virus? – computer virus definition
A computer virus is a type of computer program that, when executed, replicates itself by modifying other computer programs and inserting its own code. When this replication succeeds, the affected files/documents are then considered to be “infected” with a computer virus. A computer virus can cause extensive damage to computer data and become extremely difficult to deal with if one is not really techy.
Even though the first virus to be invented was practically harmless, the inquisitive nature of man brought about the advancement in what computer virus has become today. Some of the computer virus examples include Raila Odinga, melissa, ILOVEYOU, Sasser, and so on.
In thIs post, I will address the 9 deadliest computer viruses that vehemently destroyed businesses, and infrastructures, to mention a few.
Also Read: What Search Engine did People Use before Google?
Discover: Top Affiliate Programs to Join and Start Earning
1. Raila Odinga virus (RO):
Raila Odinga was the computer virus I first encountered, it was a common virus in Africa in early 2000.
- If you delete the picture created by RO virus, the picture would return.
- it was programmed to autorun from startup
- It creates new folder.exe folders in your computer
- It attacks the system’s 32 folders then converts the files to JPEG files
- It slows down the computer speed and freezes
It was almost an impossible virus to remove since most antivirus as of then couldn’t fight Raila Odinga. The process of removing it was later discovered and only requires more advanced steps than scanning with just antivirus.
2. Melissa computer virus:
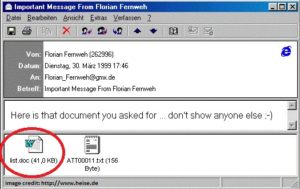
Melissa was a computer virus that began to spread in the late 90s. It was the first virus that used electronic mail to spread on a large scale, and at that period became the fastest spreading virus of all time. It was built by David L, and was spread in form of an email attachment by the name “list.doc“.
Once you click on this file, the virus then begins its spread by replicating and then attempts to seek for the Microsoft Outlook address book to e-mail itself to the first 50 names on the list with a message, “Here is that document you asked for…don’t show anyone else. In the United States, it is estimated that Melissa Virus caused losses of more than US$80 million. The virus inventor was later arrested by the FBI and was charged to court.
3. ILOVEYOU Computer Virus:
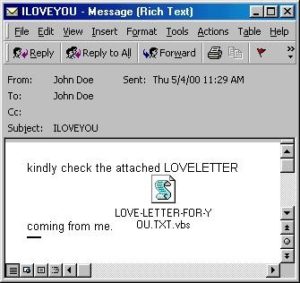
This was considered the most destructive computer virus ever created in the form of a worm. Just like other viruses, it was a standalone program capable of replicating itself. it was popularly known as ILOVEYOU. The virus was created by two Filipino programmers, Reonel Ramones and Onel de Guzman.
The virus was designed to use social engineering to get internet users to click on the attachment. The attachment was a programmed script that camouflaged as a TXT file, and has its filename as “LETTER-FOR-YOU.TXT.vbs”.
Once the file is clicked, it automatically sends itself to everyone in the user’s mailing list and proceeds to overwrite files with itself and render the computer unbootable. It was reported that the virus caused around $10 billion in damages affecting almost 10% of the world’s Internet users. The two virus inventors were never charged, as there were no laws guiding malware then.
Also read: 15 Best Free VPN for Android, iPhone and Computer Users
4. Sasser Computer Virus:
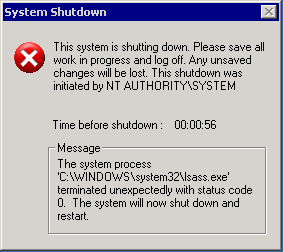
The name Sasser worm was a virus built by a computer science student named Sven Jaschan. It affected Windows OS primarily and was devastating to many critical infrastructures. The virus was designed to slow down and crash targeted computers, thereby making it hard to refresh or reset the PC without force shutting down.
It was a destructive virus that affected millions of computers. The worm played on a buffer overflow susceptibility in Local Security Authority Subsystem Service (LSASS) that monitors the safety policy of local accounts causing crashes to the computer.
The worm affected infrastructures such as; airlines, hospitals, news agencies, public transportation, etc. It was estimated to have caused over 8 billion dollars in damage recorded.
Also Read: 10 Signs of a Malware Infection on your Computer
5. My Doom Computer Virus:

My Doom was a computer virus released in 2004 and caused estimated damage of $38 billion with an adjusted inflation cost of over $52.2 billion.25% of all emails were estimated to have been infected by MyDoom in 2004. It was malware transmitted through deceitful e-mails in order to deceive the receiver as the recipient would first think that the mail is an error message since it reads ” Mail Transaction Failed “.
But, once the message is clicked upon, the malware is then executed and the worm is transferred to email addresses in the user’s address book. The malware had the ability to open random programs, thereby creating network openings that allowed access to those targeted computers. Mydoom is said to still be around today, generating 1% of all phishing emails.
6. Code Red Computer Virus
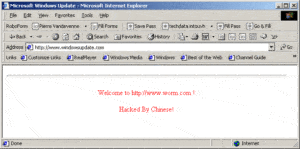
The Code Red surfaced in 2001 and was discovered by two eEye Digital Security employees. It targeted computers with a Microsoft IIS web server installed by exploiting a buffer overflow problem in the system. How this virus attack was different in this case, as it only required an active Internet connection with which it ruined the Web page that you opened by displaying a text “Hacked by Chinese!”.
Once the computer is infected, it will duplicate even more of itself and ends up eating almost all the system’s resources. It also allows backdoor access to the server, allowing for remote access to the machine.
This deadly virus brought down more than 400,000 servers including the White House web server in about one week. This virus caused total damage of over $2 billion-plus.
Also read: Pegasus Spyware – The Most Intelligent Spyware Ever Built
7. Stuxnet Computer Virus
Stuxnet is also a virus that spread through USB sticks and Microsoft Windows computers like Raila Odinga. Stuxnet worm was believed to have been in development since 2005 and was first unmasked in 2010.
The Stuxnet virus was said to have targeted a particular model of Programmable Logic Controller (PLC) which is made by Siemens. They are small industrial control systems running automated processes such as in chemical plants, on factory floors, oil refineries, and in nuclear power plants. These PLCs are controlled by computers and it is the main target of the Stuxnet worm.
Stuxnet targets supervisory control and data acquisition systems and is believed to be responsible for causing substantial damage to the Iran nuclear facilities. An article was published as of January 2020 on journalblog, stating the damages and extensive details on how a nation-state used malware to sabotage the military developments of the Iranian nation.
Also Read: The Complete difference between PayPal FnF and PayPal GnS
8. StormWorm computer virus:
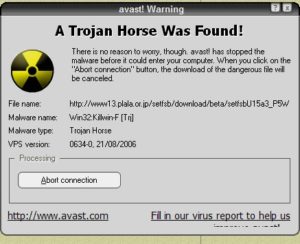
StormWorm is malware widely known as a trojan horse that attack in various name such as ( mall.dam or Trojan-Downloader.Win32.Small.dam , Troj/Dorf and Mal/Dorf , Trojan.DL.Tibs.Gen!Pac13, Trojan.Downloader-647), etc.
It was discovered in 2007 and was believed to have accounted for 8% of all malware infections globally. According to PCWorld, the Storm Worm originated from Russian. It attacked thousands of computers in Europe and the united state.
It targeted email users with a mail that reads “230 dead as storm batters Europe” and the user then gets trapped once the mail is opened, Which creates a backdoor that allows the hacker to spy and have access to the user’s data.
[ads3]
9. CryptoLocker
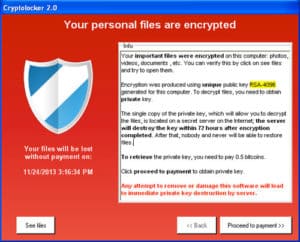
CryptoLocker is one of the computer virus examples that is a form of Trojan horse ransomware that targeted Windows. It spread through various means and once the computer is infected, it will then encrypt some of the computer files into mounted-storage connected to it with RSA public-key cryptography.
It infected over 500,000 estimated numbers and the criminal generated over $3 million from hacked users. The virus operated for some time until law enforcement agencies and security companies managed to take control part of the botnet operating CryptoLocker and Zeus. The Virus developer was later charged and the encryption keys were retrieved and released to the affected computers.
Also read: 8 Most Popular Databases for Web Development
What More? We Recommend: Best Virtual Private Network Providers
Best VPNs Categories Websites ![]() Securi
SecuriVPN/Internet Security https://www.securi.net/ ![]() CyberGhost
CyberGhostVPN/Internet Security https://www.cyberghost.com/ ![]() PrivadoVPN
PrivadoVPNVPN/Internet Security https://privadovpn.com/ ![]() AtlasVPN
AtlasVPNVPN/Internet Security https://atlasvpn.com/ ![]() Avast
AvastVPN/Internet Security https://www.avast.com/ ![]() IPVanish
IPVanishVPN/Internet Security https://www.ipvanish.com/ ![]() AVG
AVGVPN/Internet Security https://www.avg.com/ ![]() Nord VPN
Nord VPNVPN/Internet Security https://nordvpn.com/ ![]() ExpressVPN
ExpressVPNVPN/Internet Security https://www.expressvpn.com/
computer virus definition, computer virus examples, computer virus history, computer virus names, computer virus
we love to hear from you, comment below and share.





